Protecting Data-At-Rest (DAR) on mobile devices is a major concern. While the industry standard is to encrypt all data on a device, that data is decrypted and accessible after the device boots successfully. If a device is lost or stolen, a sophisticated attack can extract data from it as long as the device is still running, even if the device is locked.
Samsung created Sensitive Data Protection (SDP) to address this specific issue, and includes SDP in Samsung devices built on the Knox Platform for Enterprise (KPE).
What is Knox SDP?
With Knox SDP, selected files remain encrypted at runtime and are decrypted only after device users authenticate themselves at the device lockscreen or Knox Workspace login. Knox ejects decryption keys each time the device or Knox Workspace locks.
Why should I consider Knox SDP?
-
MDFPP-Compliant:
SDP is certified as meeting the Mobile Device Fundamentals Protection Profile (MDFPP) requirements defined by the National Information Assurance Partnership (NIAP) for DAR, meaning that SDP is approved for use by the US government and military. Without Knox SDP, the base Android system is not certified as satisfying MDFPP requirements, which mandates a form of SDP. MDFPP compliance is a requirement for many government agencies and the companies they work with. Samsung has more MDFPP-certified products than any other mobility solution provider. -
Granular Control:
App developers and enterprise IT admins can use Knox SDP to protect individual files, databases, and any other sensitive enterprise data. -
Per-App Password:
For an added layer of security, app developers and enterprise IT admins can customize Knox SDP so that sensitive data is decrypted only by a per-app password entered by the app user. In this case, the device unlock or Knox Workspace authentication alone does not decrypt app data. An app password is also needed.
How does Knox SDP work?
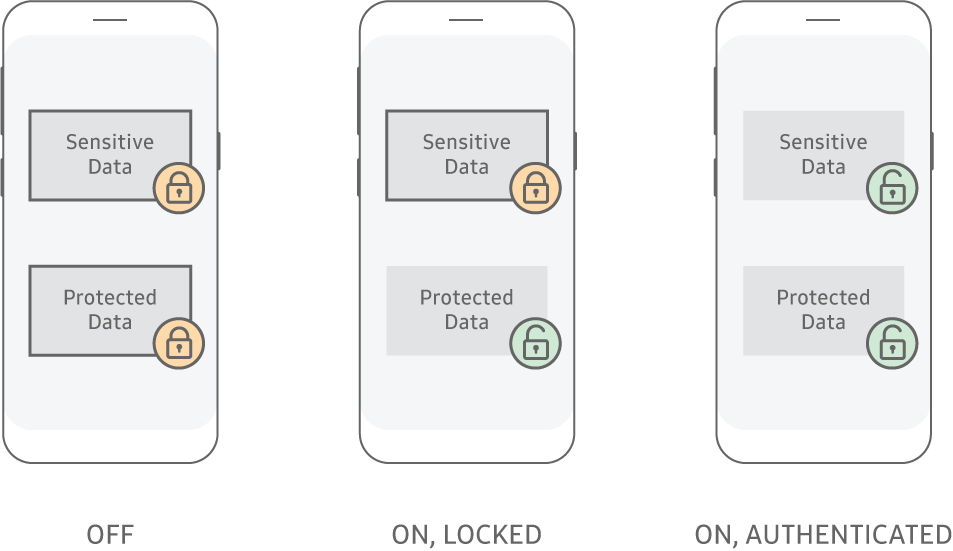
Knox’s two levels of protection and how they perform when a device is off, locked, or authenticated
The Knox Platform provides two levels of protection for Data-At-Rest:
-
Protected Data
By default, all data is encrypted when the device is powered off. When the device is powered on, the data is decrypted. The decryption key for Protected Data is tied to the device hardware, making Protected Data recoverable only on the same device. -
Sensitive Data
SDP provides an extra layer of security. Unlike Protected Data, Sensitive Data remains encrypted, even after the device boots. Data is decrypted only after the device is unlocked through user authentication. SDP data can't be decrypted in the locked state, only in the unlocked state. The SDP data decryption key is also tied to device hardware, meaning Sensitive Data is recoverable only on the same device and only after successful user authentication.
SDP enables both app developers and enterprise IT admins to label data as “sensitive” to guarantee the data is encrypted and not accessible on locked devices.
Where is Knox SDP used?
Knox SDP is enabled by default to secure the Samsung Email app's email body and attachments.
SDP even handles incoming sensitive data, such as emails and notifications, ensuring it is immediately encrypted and not accessible until the user is authenticated. This encryption uses a public key algorithm. The private key is maintained in an encrypted partition while the public part encrypts the sensitive, newly received data.
Next steps
To learn more about:
- The advantages offered by Samsung Knox devices over non-Samsung devices, see the KPE Feature Comparison Table.
- Other KPE features, see the Knox White Paper.
- Other data protection options for Samsung Knox devices, see the KPE Admin Guide.
- Other Knox solutions, see the Knox IT Solutions.